Allianz

Bridgestone

Ford

Travelers

Verizon

British Telecom

Insulet Corporation
Webinar
Top Things You Need To Know About API Security
Analyst Report
How to Scale API Security for Telecoms Industry from TAG analysts
Fix APIs Today,
Prevent Breaches Tomorrow
Automate and scale the enforcement of API security policies and standards across distributed development and security ecosystems
Governance
Security teams enforce security policy compliance
Acceleration
Remove security bottlenecks and speed up innovation
Automation
Remove manual intervention and speed up delivery
Scalable
Protect 1000s of your APIs from the design to runtime
Security
Shift-Left with API security testing for developers
Proactive
Proactive security model removes false positives

42Crunch's ability to secure both the CI/CD pipeline & the runtime environment makes it a compelling candidate for any API security project. Rick Turner
Principal Analyst

Helping Security
& Development Teams
The only API security platform that enforces governance and compliance from design to runtime and gives developers the tools to code security from inside the IDE
API Capture automates the generation of OpenAPI contracts and API security testing configurations from Postman collections and API traffic.
- Free up development teams from time-consuming design and maintenance tasks
- Automate security test cofigurations
- Use OpenAPI specification to improve API documentation
- Capture unknown traffic and reconcile OpenAPI definitions with real traffic to improve governance
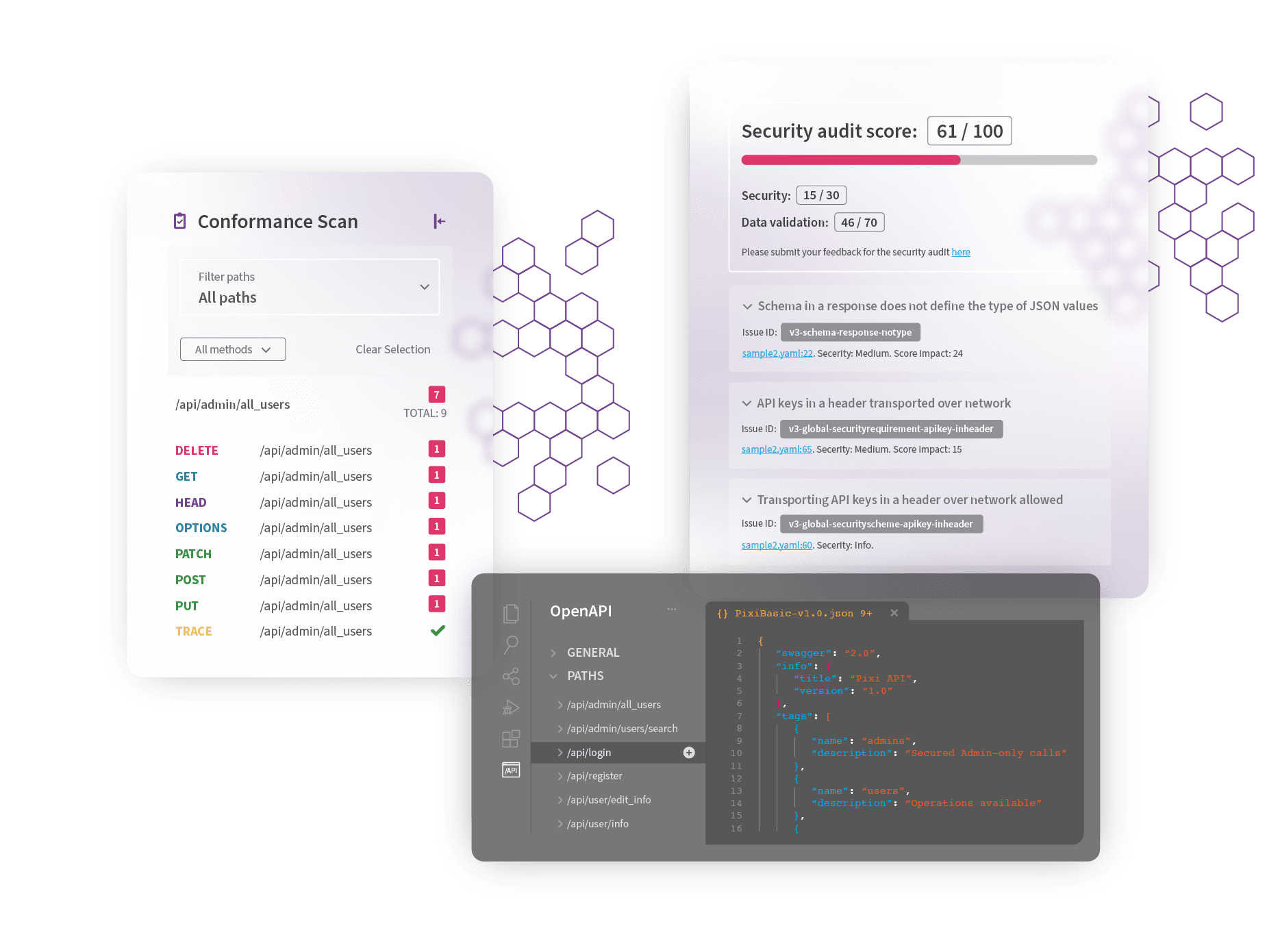
- 300+ security checks
- Actionable report with zero false positives
- Available from IDEs and CI/CD pipelines
- Instant visibility into API security status
- Test live endpoints
- Early identification of OWASP API Security Top 10 issues
API Protect offers runtime API security policy enforcement with a low footprint, containerized micro-API firewall.
- API Protect is configured in one-click from the API contract
- The API Contract becomes the white list for security
- No need to guess via AI/ML which traffic is valid
- No policies to write
Ready for DevSecOps
Push your OpenAPI definition to your CI/CD pipeline and automatically audit, scan and protect your APIs
Developers Use Our Tools
Industry's #1 OpenAPI (Swagger) Editor and API Security Audit tool are available on your favorite IDEs



Some Industry Insights
Free Industry Analyst Reports covering 42Crunch and API Security
Survey of IT & business leaders to understand their views on API Security
#1 API Security Community
Join your security peers and get the industry’s leading APISecurity.io newsletter every fortnight.
Ready to Learn More?
Developer-first solution for delivering API security as code.